If IOMMU disrupt remapping is not sustained on your cpu, you will have to set up unsafe disrupts on your Proxmox VE server to passthrough PCI/PCIE gadgets on Proxmox VE digital makers.
Add the following line in the iommu_unsafe_interrupts. conf documents and press
alternatives vfio_iommu_type 1 allow_unsafe_interrupts= 1
As soon as you’re done, you should upgrade the initramfs of your Proxmox VE server.
What to do if my GPU (or PCI/PCIE Tool) is not in its own IOMMU Team?
If your server has numerous PCI/PCIE ports, you can relocate the GPU to a different PCI/PCIE port and see if the GPU is in its very own IOMMU group.
If that does not function, you can attempt enabling the a/c override bit patch on Proxmox VE.
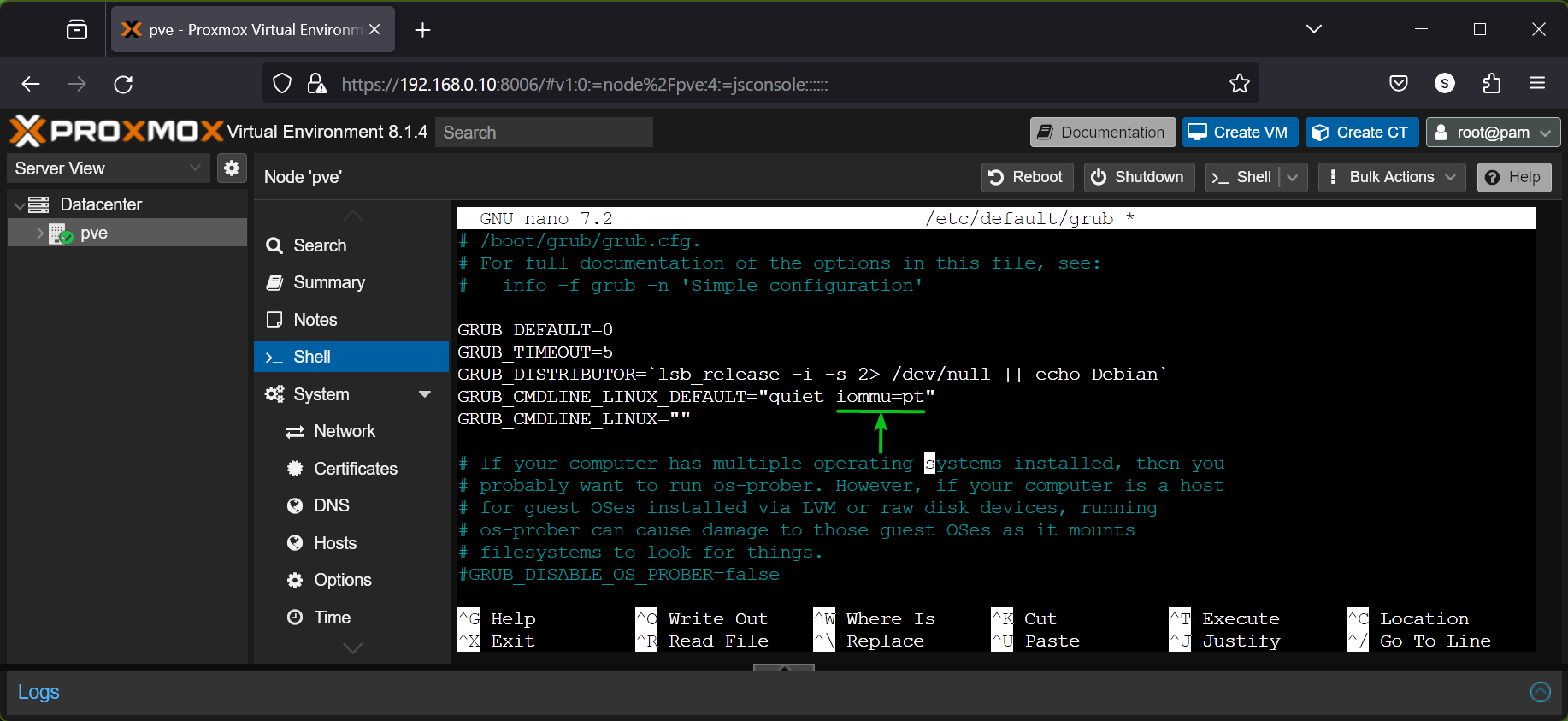
To try enabling the a/c override kernel spot on Proxmox VE, open the / etc/default/grub documents with the nano text editor as adheres to:
Include the kernel boot choice pcie_acs_override=downstream at the end of the GRUB_CMDLINE_LINUX_DEFAULT
When you’re done, press
You ought to have far better IOMMU grouping as soon as your Proxmox VE server boots.
If your GPU still does not have its very own IOMMU team, you can go one action additionally by using the pcie_acs_override=downstream, multifunction instead. You need to have an also much better IOMMU collection.
If pcie_acs_override=downstream, multifunction cause far better IOMMU grouping that pcie_acs_override=downstream , then why usage pcie_acs_override=downstream in all?
Well, the objective of PCIE ACS override is to deceive the kernel into assuming that the PCIE tools are isolated when they are not in reality. So, PCIE ACS override features safety and security and stability problems. That’s why you should try utilizing a much less hostile PCIE air conditioner override option pcie_acs_override=downstream initially and see if your problem is fixed. If pcie_acs_override=downstream does not function, only after that you should utilize the much more aggressive alternative pcie_acs_override=downstream, multifunction
Just how do I Blacklist AMD GPU Drivers on Proxmox VE?
If you intend to passthrough an AMD GPU on Proxmox VE online makers, you must blacklist the AMD GPU chauffeurs and make sure that it makes use of the VFIO vehicle driver rather.
Initially, open up the / etc/modprobe. d/blacklist. conf documents with the nano full-screen editor as complies with:
$ nano/ etc/modprobe. d/blacklist. conf
To blacklist the AMD GPU motorists, include the complying with lines to the / etc/modprobe. d/blacklist. conf file and press
blacklist amdgpu
When you’re done, you must upgrade the initramfs of your Proxmox VE web server for the adjustments to take effect.
How do I Blacklist NVIDIA GPU Drivers on Proxmox VE?
If you wish to passthrough an NVIDIA GPU on Proxmox VE online devices, you must blacklist the NVIDIA GPU motorists and make sure that it uses the VFIO vehicle driver rather.
Initially, open up the / etc/modprobe. d/blacklist. conf data with the nano text editor as follows:
$ nano/ etc/modprobe. d/blacklist. conf
To blacklist the NVIDIA GPU motorists, include the following lines to the / etc/modprobe. d/blacklist. conf file and press
blacklist nvidia
blacklist nvidiafb
blacklist nvidia_drm
Once you’re done, you should upgrade the initramfs of your Proxmox VE server for the changes to work.
Just how do I Blacklist Intel GPU Drivers on Proxmox VE?
If you want to passthrough an Intel GPU on Proxmox VE digital equipments, you have to blacklist the Intel GPU chauffeurs and ensure that it uses the VFIO driver instead.
First, open the / etc/modprobe. d/blacklist. conf data with the nano full-screen editor as adheres to:
$ nano/ etc/modprobe. d/blacklist. conf
To blacklist the Intel GPU drivers, add the complying with lines to the / etc/modprobe. d/blacklist. conf file and press
blacklist snd_hda_codec_hdmi
blacklist i 915
Once you’re done, you should update the initramfs of your Proxmox VE web server for the adjustments to take effect.
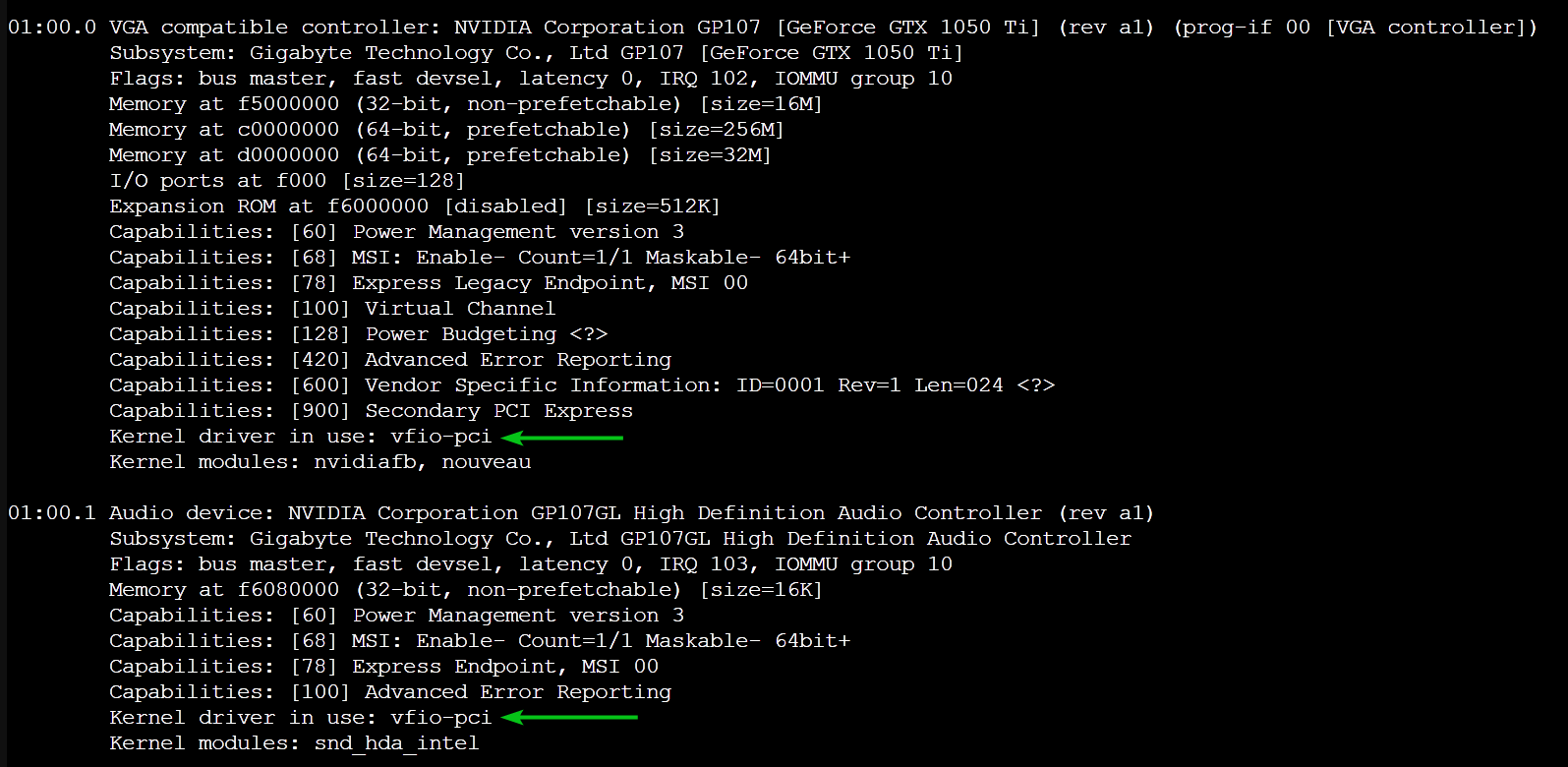
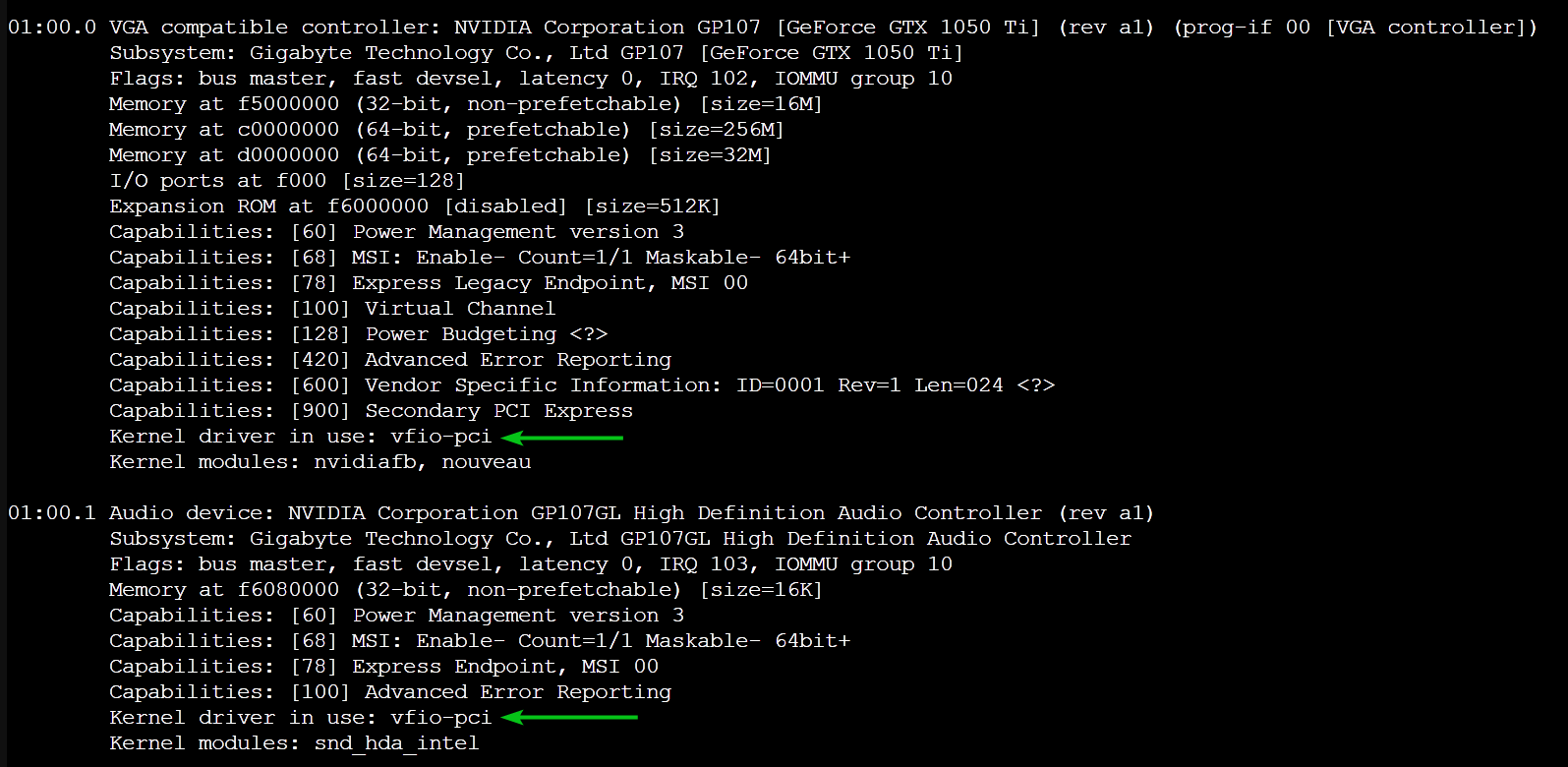
Just how to Inspect if my GPU (or PCI/PCIE Device) is Making Use Of the VFIO Motorist on Proxmox VE?
To check if your GPU or desired PCI/PCIE gadgets are using the VFIO driver, run the adhering to command:
If your GPU or PCI/PCIE device is using the VFIO chauffeur, you must see the line Kernel vehicle driver in use: vfio-pci as noted in the screenshot listed below.
I Have Blacklisted the AMU GPU Drivers, Still, the GPU is not Making Use Of the VFIO Driver, What to Do?
Sometimes, blacklisting the AMD GPU vehicle drivers is not enough, you additionally have to configure the AMD GPU vehicle drivers to load after the VFIO vehicle driver.
To do that, open the / etc/modprobe. d/vfio. conf documents with the nano text editor as complies with:
$ nano/ etc/modprobe. d/vfio. conf
To set up the AMD GPU drivers to tons after the VFIO driver, include the adhering to lines to the / etc/modprobe. d/vfio. conf data and press
softdep amdgpu pre: vfio-pci
As soon as you’re done, you need to update the initramfs of your Proxmox VE web server for the changes to work.
I Have Blacklisted the NVIDIA GPU Drivers, Still, the GPU is not Utilizing the VFIO Driver, What to Do?
At times, blacklisting the NVIDIA GPU motorists is insufficient, you also have to configure the NVIDIA GPU motorists to lots after the VFIO motorist.
To do that, open up the / etc/modprobe. d/vfio. conf data with the nano text editor as complies with:
$ nano/ etc/modprobe. d/vfio. conf
To configure the NVIDIA GPU vehicle drivers to lots after the VFIO driver, include the following lines to the / etc/modprobe. d/vfio. conf data and press
softdep nvidia pre: vfio-pci
softdep nvidiafb pre: vfio-pci
softdep nvidia_drm pre: vfio-pci
softdep drm pre: vfio-pci
When you’re done, you need to upgrade the initramfs of your Proxmox VE web server for the modifications to work.
I Have Blacklisted the Intel GPU Drivers, Still, the GPU is not Using the VFIO Motorist, What to Do?
At times, blacklisting the Intel GPU vehicle drivers is not nearly enough, you also need to configure the Intel GPU chauffeurs to load after the VFIO vehicle driver.
To do that, open the / etc/modprobe. d/vfio. conf data with the nano text editor as follows:
$ nano/ etc/modprobe. d/vfio. conf
To set up the Intel GPU chauffeurs to lots after the VFIO motorist, include the adhering to lines to the / etc/modprobe. d/vfio. conf file and press
softdep snd_hda_codec_hdmi pre: vfio-pci
softdep i 915 pre: vfio-pci
As soon as you’re done, you have to update the initramfs of your Proxmox VE server for the adjustments to take effect.
Solitary GPU Used VFIO Motorist, However When Configured a Second GPU, it Really Did Not Job, Why?
In the / etc/modprobe. d/vfio. conf documents, you need to add the IDs of all the PCI/PCIE tools that you wish to use the VFIO motorist in a solitary line. One device per line will not function.
For example, if you have 2 GPUs that you want to configure to make use of the VFIO motorist, you have to add their IDs in a single line in the / etc/modprobe. d/vfio. conf documents as follows:
If you intend to add an additional GPU to the checklist, simply add it at the end of the existing vfio-pci line in the / etc/modprobe. d/vfio. conf file as adheres to:
alternatives vfio-pci ids=
Never do this. Although it looks much cleaner, it won’t work. I do wish we might define PCI/PCIE IDs this way.
choices vfio-pci ids=
alternatives vfio-pci ids=
Why Disable VGA Adjudication for the GPUs and How to Do It?
If you’re utilizing UEFI/OVMF BIOS on the Proxmox VE digital device where you wish to passthrough the GPU, you can disable VGA adjudication which will certainly lower the tradition codes called for during boot.
To disable VGA arbitration for the GPUs, add disable_vga= 1 at the end of the vfio-pci choice in the / etc/modprobe. d/vfio. conf data as shown listed below:
choices vfio-pci ids=
What if my GPU is Still not Using the VFIO Chauffeur Also After Configuring VFIO?
Also after doing every little thing correctly, if your GPU still does not use the VFIO vehicle driver, you will certainly need to attempt starting Proxmox VE with bit alternatives that disable the video clip framebuffer.
On Proxmox VE 7 1 and older, the nofb nomodeset video clip=vesafb: off video=efifb: off video=simplefb: off bit alternatives disable the GPU framebuffer for your Proxmox VE server.
On Proxmox VE 7 2 and newer, the initcall_blacklist=sysfb_init bit choice does a much better work at disabling the GPU framebuffer for your Proxmox VE server.
Open the GRUB bootloader configuration file / etc/default/grub data with the nano text editor with the following command:
Include the kernel choice initcall_blacklist=sysfb_init at the end of the GRUB_CMDLINE_LINUX_DEFAULT
As soon as you’re done, press
GPU Passthrough Showed No Mistakes, But I’m Getting a Black Display on the Screen Connected to the GPU Passed to the Proxmox VE VM, Why?
As soon as you’ve passed a GPU to a Proxmox VE digital machine, make sure to utilize the Default Graphics card before you begin the virtual maker. In this manner, you will be able to access the screen of the virtual device from the Proxmox VE web monitoring UI, download and install the GPU motorist installer on the online maker, and mount it on the online device.
When the GPU driver is installed on the virtual maker, the display of the virtual device will certainly be displayed on the display linked to the GPU that you’ve passed to the virtual equipment also.
Remember, never ever use SPICE, VirtIO GPU, and VirGL GPU Show Graphic card on the Proxmox VE virtual equipment that you’re configuring for GPU passthrough as it has a high chance of failure.
What is AMD Vendor Reset Pest and How to Fix it?
AMD GPUs have a popular pest called “vendor reset insect”. As Soon As an AMD GPU is passed to a Proxmox VE online device, and you power off this online maker, you won’t have the ability to utilize the AMD GPU in one more Proxmox VE digital equipment. At times, your Proxmox VE web server will certainly come to be less competent because of this. This is called the “supplier reset bug” of AMD GPUs.
The factor this takes place is that AMD GPUs can’t reset themselves correctly after being passed to a digital maker. To repair this problem, you will need to reset your AMD GPU appropriately. To learn more on setting up the AMD supplier reset on Proxmox VE, read this write-up and review this thread on Proxmox VE online forum. Also, inspect the supplier reset GitHub page.
Exactly how to Provide a vBIOS for the Passed GPU on a Proxmox VE Virtual Maker?
If you have actually set up the GPU on the very first port of your motherboard, you may not have the ability to passthrough the GPU in a Proxmox VE virtual equipment by default. Some motherboards shadow the vBIOS of the GPU set up on the first slot by default which is the factor the GPU set up on the initial slot of those motherboards can’t be passed to digital devices.
The option to this trouble is to install the GPU on the second port of the motherboard, extract the vBIOS of the GPU, mount the GPU on the initial port of the motherboard, and passthrough the GPU to a Proxmox VE digital equipment along with the extracted vBIOS of the GPU.
KEEP IN MIND: To find out exactly how to draw out the vBIOS of your GPU, review this article
As soon as you have actually gotten the vBIOS for your GPU, you should store the vBIOS file in the / usr/share/kvm/ directory site of your Proxmox VE server to gain access to it.
Once the vBIOS file for your GPU is stored in the / usr/share/kvm/ directory, you need to configure your virtual machine to utilize it. Currently, there is no other way to define the vBIOS declare PCI/PCIE tools of Proxmox VE online makers from the Proxmox VE internet management UI. So, you will have to do whatever from the Proxmox VE shell/command-line.
You can find the Proxmox VE online device setup files in the / etc/pve/qemu-server/ directory site of your Proxmox VE server. Each Proxmox VE digital device has one setup documents in this directory in the format
For example, to open the Proxmox VE digital equipment setup data (for editing and enhancing) for the virtual equipment ID 100, you will certainly require to run the complying with command:
$ nano/ etc/pve/qemu-server/ 100 conf
In the virtual maker setup data, you will need to add romfile=
As an example, if the vBIOS filename for my GPU is gigabyte-nvidia- 1050 ti.bin , and I have actually passed the GPU on the first port (slot 0) of the digital maker ( hostpci0 , then in the 100 conf data, the line ought to be as complies with:
Once you’re done, conserve the digital device setup documents by pressing
What to do if Some Apps Crash the Proxmox VE Windows Virtual Equipment?
Some apps such as GeForce Experience, Passmark, and so on may crash Proxmox VE Windows online makers. You may also experience an unexpected blue screen of death (BSOD) on your Proxmox VE Windows virtual devices. The reason it takes place is that the Windows digital machine may try to access the model-specific registers (MSRs) that are not really readily available and relying on just how your hardware manages MSRs requests, your system may collapse.
The option to this issue is disregarding MSRs messages on your Proxmox VE web server.
To configure MSRs on your Proxmox VE server, open up the / etc/modprobe. d/kvm. conf file with the nano full-screen editor as complies with:
$ nano/ etc/modprobe. d/kvm. conf
To neglect MSRs on your Proxmox VE web server, add the complying with line to the / etc/modprobe. d/kvm. conf documents.
choices kvm ignore_msrs= 1
When MSRs are neglected, you could see a lot of MSRs alerting messages in your dmesg system log. To stay clear of that, you can disregard MSRs as well as disable logging MSRs advising messages by adding the following line instead:
alternatives kvm ignore_msrs= 1 report_ignored_msrs=0
Once you’re done, press
How to Solve HDMI Audio Crackling/Broken Troubles on Proxmox VE Linux Virtual Machines?
If you have actually passed the GPU to a Linux Proxmox VE virtual machine and you’re getting poor audio quality on the virtual maker, you will require to enable MSI (Message Signal Interrupt) for the audio device on the Proxmox VE digital machine.
To enable MSI on the Linux Proxmox VE online equipment, open up the / etc/modprobe. d/snd-hda-intel. conf data with the nano full-screen editor on the virtual machine with the following command:
$ sudo nano/ etc/modprobe. d/snd-had-intel. conf
Include the complying with line and conserve the file by pushing
options snd-hda-intel enable_msi= 1
For the adjustments to work, reboot the Linux online device with the adhering to command:
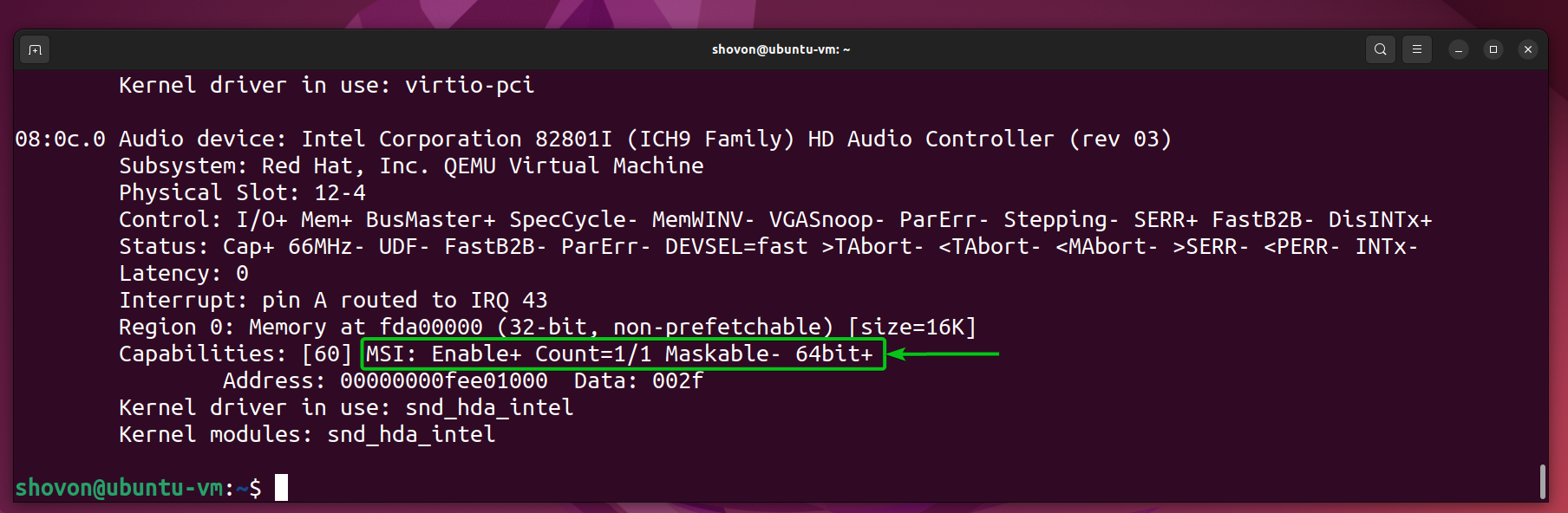
When the digital maker boots, inspect if MSI is allowed for the audio gadget with the following command:
If MSI is allowed for the audio device on the digital equipment, you should see the marked line in the audio tool details.

How to Update Proxmox VE initramfs?
Every single time you make any kind of adjustments to documents in the / etc/modules-load. d/ and / etc/modprobe. d/ directories, you must update the initramfs of your Proxmox VE 8 setup with the adhering to command:
$ update-initramfs -u -k all
When Proxmox VE initramfs is updated, reboot your Proxmox VE server for the changes to work.
Exactly How to Update Proxmox VE GRUB Bootloader?
Every single time you update the Proxmox VE GRUB boot configuration documents / etc/default/grub , you should upgrade the GRUB bootloader for the adjustments to work.
To upgrade the Proxmox VE GRUB bootloader with the new arrangements, run the adhering to command:
Once the GRUB bootloader is upgraded with the brand-new configuration, reboot your Proxmox VE server for the adjustments to take effect.
Conclusion
In this article, have gone over a few of the most typical Proxmox VE PCI/PCIE passthrough and GPU passthrough troubles and the actions you can take to address those problems.
Recommendations
- [TUTORIAL]– PCI/GPU Passthrough on Proxmox VE 8: Installation and configuration|Proxmox Support Forum
- Ultimate Novice’s Overview to Proxmox GPU Passthrough
- Reviewing and Writing Model Details Registers in Linux
- The MSI Motorist Overview HOWTO– The Linux Kernel paperwork